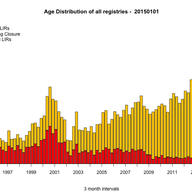
K-root Expansion Plan


Romeo Zwart
Based in Amsterdam (NL)
Former manager of the Global Information Infrastructure team at the RIPE NCC. More
• 9 min read
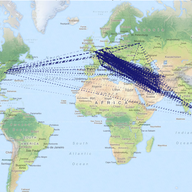
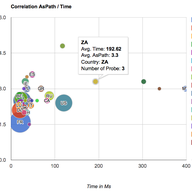
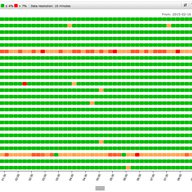
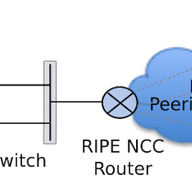
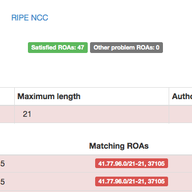
We're getting ready to expand K-root coverage, and we'll soon be inviting interested members of the community to express their interest in hosting their own K-root node. Learn more about how we propose expanding the network, what the requirements are for hosting your own K-root node, and the projec…