You’ve Got the Power: Sustainable Procurement and the RIPE Community


Michael Oghia
Based in Belgrade, Serbia
Michael J. Oghia is an entrepreneur, tech sustainability consultant, and the founder of Oghia Advising – an independent agency offering services to clients across Europe, North America, and beyond within the digital infrastructure, cyber resilience, Internet governance & policy, and media development sectors. He is a connector at heart and … More
• 8 min read
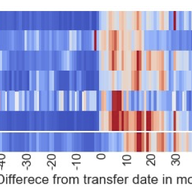
The RIPE community can contribute to a more sustainable Internet in multiple ways, but one of the most immediate and impactful among these involves decisions regarding buying hardware and sourcing services. We take a closer look at the issues surrounding procurement, the resources available, and ex…