Krill Gains Powerful ROA Management Based on BGP Routing
• 5 min read
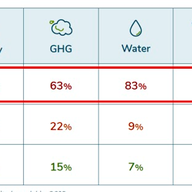
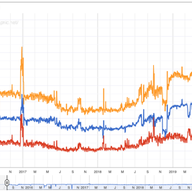
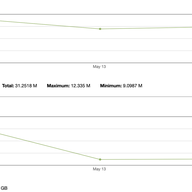
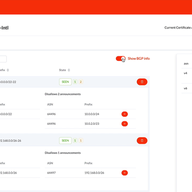
Over the last two years NLnet Labs has been working on free, open source RPKI software and research for the community, supported by the RIPE NCC Community Projects Fund. We are incredibly excited that six months after the first release of Krill it already powers delegated RPKI for over 150 organisa…