How Consumer IoT Devices Expose Information


Anna Maria Mandalari
Based in London
Anna Maria Mandalari works as Assistant Professor at University College London (UCL). She is affiliated with the Electronic & Electrical Engineering Department and member of the UCL’s Academic Center of Excellence in Cyber Security Research (ACE-CSR). She is Honorary Research Fellow at the Institute for Security Science and Technology at … More
• 11 min read
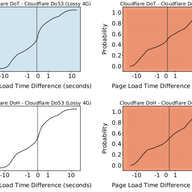
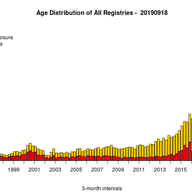
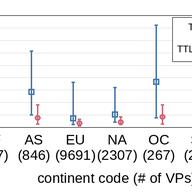
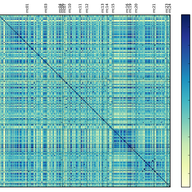
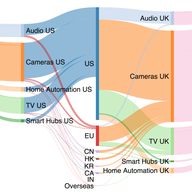
Do our Internet-of-Things (IoT) devices at home expose private information unexpectedly? Do leaks of sensitive user data depend on the location and jurisdiction of the IoT device? Through a total of 34,586 rigorous automated and manual controlled experiments, we characterised information exposure f…