Exploring RIPE Atlas Traceroutes from 2012 to 2019


Nevil Brownlee
Based in Taupo, New Zealand
Nevil started work at the University of Auckland's Computer Centre in 1971, developed the University's internal network, then the Kawaihiko ( NZ Universities) network, which used NeTraMet, his Traffic Flow Monitoring system. He has been active in the IETF since 1992. From 1990 onward he's been a CAIDA Staff member. … More
• 29 min read
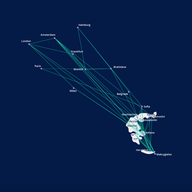
This analysis of RIPE Atlas traceroutes for days in 2012, 2015, 2017 and 2019 displays full network graphs for each successive half-hour and develops an algorithm for finding node or edge outages of an hour or more.