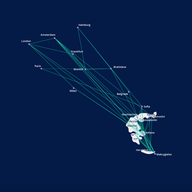
IPv6 Support on the PlayStation 5


Tore Anderson
Based in Oslo, Norway
Network architect and administrator for Redpill Linpro, an application and server operations and data centre hosting provider operating in the Nordic countries. More
• 5 min read
With the arrival of the next generation of gaming consoles, has progress been made toward better IPv6 capability?