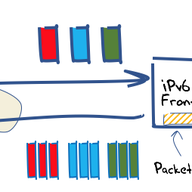
IoT Turning Evil

Ivana Tomic
Based in London
Dr Ivana Tomic is currently working as a Research Associate in the AESE group at Imperial College London. She received her PhD in Control Theory from City, University of London in October 2016 where she worked on the implementation of distributed control algorithms in multi-agent networks. Her research interests include … More
• 7 min read
Internet of Things (IoT) emerged as a complex cyber-physical system that allows smart devices to sense the environment and modify it accordingly to enhance the way we work and live. The existence of such a large network of interconnected entities poses major security and privacy issues that prevent…