Multi-level MDA-Lite Paris Traceroute
• 8 min read
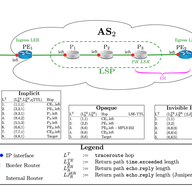
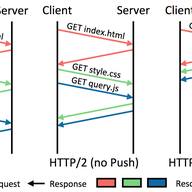
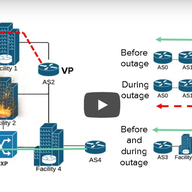
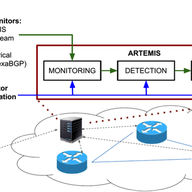
On-path load balancing can send traffic across many potential paths, which typical traceroute usage will not fully capture. We are working on algorithms for a more complete traceroute across load-balanced paths, and we are interested in deployment on RIPE Atlas. We'd like your feedback.