BGP Zombies


Romain Fontugne
Based in Tokyo
I am the deputy director of IIJ Research Laboratory. The focus of my work is on Internet measurements, data analysis, and routing. More
• 8 min read
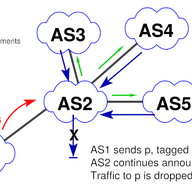
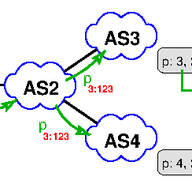
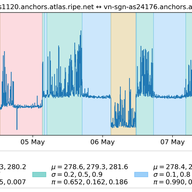
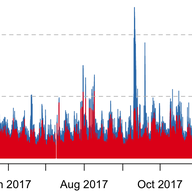
When withdrawing an IP prefix from the Internet, an origin network sends BGP withdraw messages, which are expected to propagate to all BGP routers that hold an entry for that IP prefix in their routing table. Yet network operators occasionally report issues where routers maintain routes to IP prefi…