DDoS Hide & Seek: On the Effectiveness of a Booter Services Takedown

Daniel Kopp is a member of the DE-CIX Research and Development team since 2015. He participates in several national and international research activities, such as EU or federal funded projects. His research interests are Internet and network measurements, as well as Internet and computer security. He actively contributes to the … More
• 9 min read
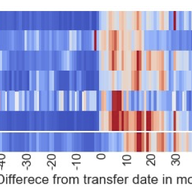
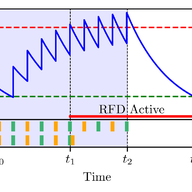
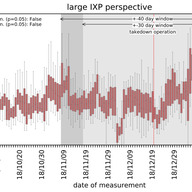
In this article, we investigated booter-based DDoS attacks in the wild and the impact of an FBI takedown targeting fifteen booter websites in December 2018. We investigated and compared attack properties of multiple booter services by launching DDoS attacks against our own infrastructure. To unders…