Navigating Network Measurements - A Review of Results and Services

I am a system administrator turned network & security researcher, looking at digital infrastructures & society, and operators. Currently working at the Max-Planck Institut for Informatics as a senior researcher; Usually speaking for myself and not my affiliation. More
• 6 min read
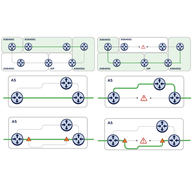
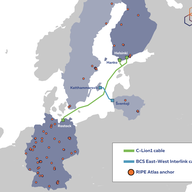
Following up on our previous article looking into the goals and infrastructure behind measurement.network, this time we're going over the services that were made available last year and the research done so far.